Baking in cybersecurity for air taxis
November 2022
By now, it should be obvious that no sector of society is immune to cyberattacks. And yet, the legions of companies that are planning the electric air taxi revolution spend far more time showing off their cabin designs and flight ranges than bragging about their cybersecurity plans. Architects of these aircraft and the traffic management system must plan now for cybersecurity, say three authors from the Institute for Public Research, part of the nonprofit CNA Corporation based in Virginia.
It’s the year 2045. In urban centers, electrically powered air taxis have become commonplace and have drastically eased surface road traffic. A trip across town that had typically been filled with red lights and traffic can now be quickly accomplished by flying above the city in special corridors. Areas where public transportation had been less accessible now have hubs where these advanced vehicles offer access to travel in ways not possible before.
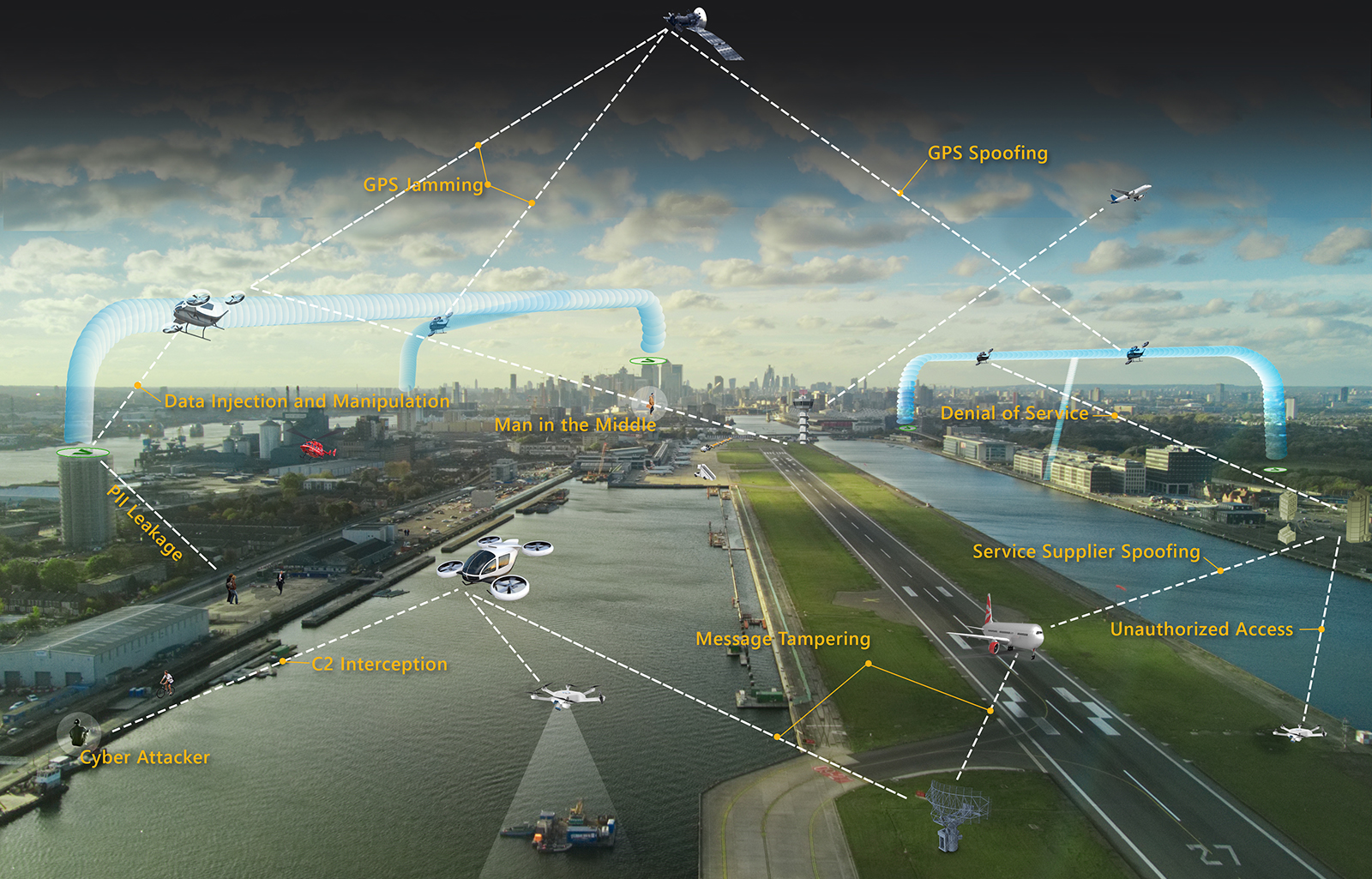
Urban air mobility is arguably the most exciting part of today’s advanced air mobility movement. Companies are flying prototypes of their aircraft; FAA is deliberating over the regulations for certification; the basics of a traffic management approach have been established. This progress is driven by the fact that UAM promises to unlock a variety of societal advances. But those benefits cannot be achieved unless this sector immediately takes steps to “bake in” cybersecurity from the start. An attack on UAM infrastructure, such as the communications links or navigation data, could have devastating consequences that endanger UAM passengers and potentially result in the loss of lives. Such an incident in the early stages of UAM would demoralize the public’s confidence and could disrupt the sector’s viability altogether.
The first iterations of UAM aircraft will retain pilots aboard for purposes of FAA certification, but subsequent versions could well be monitored from the ground with no pilot aboard. Either way, existing aircraft traffic management techniques cannot be scaled up to meet the coming UAM demand, and this is forcing the aviation industry to think innovatively about how to manage UAM traffic. As a starting point, FAA released a Concept of Operations for UAM in June 2020 based on collaboration with NASA and the industry. The proposed management of UAM traffic follows a similar approach to that planned for small uncrewed aircraft: Regulators will set forth operational requirements, and a collection of industry service suppliers will work together to ensure aircraft are safely separated in the skies. Whatever form the final concept takes, communications among aircraft and to the ground infrastructure will be key, and as the industry strives for greater automation, aircraft will become more reliant on software and computers, making the vehicles and traffic management scheme juicy targets.
Why would anyone attack this infrastructure or the aircraft within it? Researchers project that the UAM market will continue to grow across the globe and by 2030 will achieve an annual valuation upward of $6.5 billion in the United States. Such a lucrative and transformative component of the transportation infrastructure inherently becomes a highly attractive target. Incidents such as the May 2021 Colonial Oil Pipeline ransomware attack highlight the damaging consequences of being unprepared for an attack on key infrastructure. As society becomes increasingly reliant on digital technologies, the attack surface continues to expand, presenting an increasing threat of cyberattacks.
Due to the increased reliance on industry providers for services typically provided centrally by FAA in its highly secured network, there will be a larger cyberattack surface for UAM than in traditional aviation. That translates to more potential entry points for attackers compared to traditional air traffic managed by a single entity. UAM stakeholders must conduct an in-depth assessment of the entire UAM ecosystem spanning cloud servers, aircraft and software to include navigation algorithms and patches, and other processes or capabilities supporting UAM operations.
We have been alerting the UAM industry to the cyber threat since 2021, when CNA initiated a study with support from NASA that led to the white paper, “Cybersecurity of a Federated Airspace.” We leveraged the National Institute for Standards and Technology Cybersecurity Framework, which provides guidance and a common set of terminology and mechanisms to help organizations manage risks to critical infrastructure. The framework defines and provides guidance about five “core functions”: identify ecosystem needs to manage cybersecurity risk; protect against cybersecurity risks to ecosystem resources; and detect, respond to and recover from a cybersecurity event. These functions are relevant to any critical infrastructure, including UAM environments, and provide a comprehensive method of addressing cybersecurity risks that considers the business, implementation and operations levels.
A day in the life
Cybersecurity mechanisms will need to be unmistakably but inconspicuously integrated into the everyday UAM experience. Ahead, we present a typical UAM flight and provide examples of how the NIST core functions should be present throughout the journey to win the confidence of the general public.
- It’s 8 a.m. You check your mobile app to see that you’re next in line at the neighborhood vertiport. You board the next available air taxi and sync your phone to the onboard Wi-Fi so that your route appears on the screen. As the flight takes off, you remark to yourself, “The navigation interface looks different today; I see some new processes that seem to be running in the background. I wonder if there was an upgrade?”
Indeed, in the future, many UAM vehicles will incorporate third-party vendors that rely on upstream libraries requiring periodic updates. The use of third-party components will result in a very complex supply chain that is difficult to secure and can be susceptible to cyberattacks. Future UAM service providers must secure supply chains at all levels in the ecosystem by proactively identifying vulnerabilities. As seen in the 2020 SolarWinds cybersecurity breach, malicious code injected into upstream software can have widespread impacts on downstream applications.
- After some pondering, you look outside the window and notice a few air taxis nearby that are operated by a competing company. You think, “That air taxi to the west looks like it’s coming my way. How do all these different companies communicate with each other to avoid colliding?”
Communication will be a foundational component of the future UAM ecosystem, especially due to its federated nature. To ensure all communication is secure against attacks such as spoofing, future UAM requirements should follow a zero-trust approach. Zero-trust, as its name implies, assumes that an attacker has already compromised your network, and all security decisions are made based on this notion. Therefore, all other parties are not automatically trusted, requiring all communications to be effectively protected to ensure that the entity with whom you are communicating is indeed the correct entity.
- The neighboring air taxi makes a turn to the north, so you settle in and check the morning news on your phone. While you are relaxing, the taxi continues en route and hums as its systems process information.
In the future UAM ecosystem, vehicles will constantly send, receive and monitor communications to detect anything out of the ordinary. For example, a series of unexpected requests coming from an unusual IP address may warrant further inspection. To distinguish between normal and abnormal situations, service providers will need to develop baselines of acceptable and expected behavior that can be used as a comparison to detect for anomalies that may indicate unintended intrusions. Baseline data will define typical characteristics such as frequency, type, format and content of data exchanged between vehicles or service providers. Because UAM will be a novel, nonoperational ecosystem, the development of comprehensive baseline data will be a difficult but critical challenge as the industry advances.
- You look up from your phone and realize the air taxi is hovering. Unbeknownst to you, your destination vertiport detected a possible denial-of-service attack and asked operators to consider landing at a nearby vertiport. You wonder, “What’s going on?”
To effectively mitigate impacts in this future ecosystem, UAM systems including service providers, vehicles and operators, and infrastructure will need to be programmed to respond to detected cybersecurity events by immediately alerting nearby systems, as well as industry and government stakeholders. This communication about cybersecurity incidents will be critical to ensuring all stakeholders maintain awareness of any vulnerabilities or threats. The expected number and diversity of future UAM stakeholders will be vast and will render accurate and timely communication more challenging. They will need to develop incident response plans that detail the necessary communication protocols in the case of attacks.
- The attack is quickly resolved, and your air taxi continues toward your destination. You gather your belongings and are ready to alight from the vehicle as soon as the doors open.
UAM stakeholders will need to develop protocol to assess the recovery process of any affected system to actively process and learn from cybersecurity events. These protocols should assess how the situation was handled and identify actions that were successful and areas that can be enhanced in future recovery activities. In addition, each stakeholder should track a series of recovery metrics, such as the mean time to recovery, to monitor the ability of the UAM operational environment to recover. These metrics will be important for ensuring that cybersecurity events are addressed in a timely manner and improving future recovery rates.
Looking forward
Thanks to these cybersecurity measures, our passenger’s air taxi journey was incident-free, aside from a short pause in operations. The average user of UAM systems is blissfully ignorant of the hard-working personnel and systems behind the scenes who have evaluated, engineered, planned and developed cybersecurity protocols to thwart attempted attacks. Integrating cybersecurity across the UAM ecosystem involves designing protocols for secure information sharing, testing for interoperability beginning from the earliest stages and setting up how to identify the good actors from the bad from the start. Stakeholders must plan now for cybersecurity events, being proactive rather than reactive in applying solutions to prevent the UAM equivalent of the Colonial Pipeline attack from ever occurring.
Adam Monsalve
is a cybersecurity analyst at CNA Corporation’s Institute for Public Research. He has a doctorate in materials science and engineering from the University of Florida.

Rebekah Yang
is a systems engineer at CNA Corporation’s Institute for Public Research. She has a doctorate in civil engineering from the University of Illinois.

Addam Jordan
is chief scientist of the Enterprise Systems and Data Analysis division in CNA Corporation’s Institute for Public Research. He has a master’s degree in systems engineering and integration from George Washington University and a bachelor’s in aviation and air traffic control from Hampton University.